A first known instance of ransomware on Mac computers was discovered this week by researchers at Palo Alto. They discovered the OS X KeRanger malware on March 4 and, to date, it has been the only ransomware to successfully target Mac users.
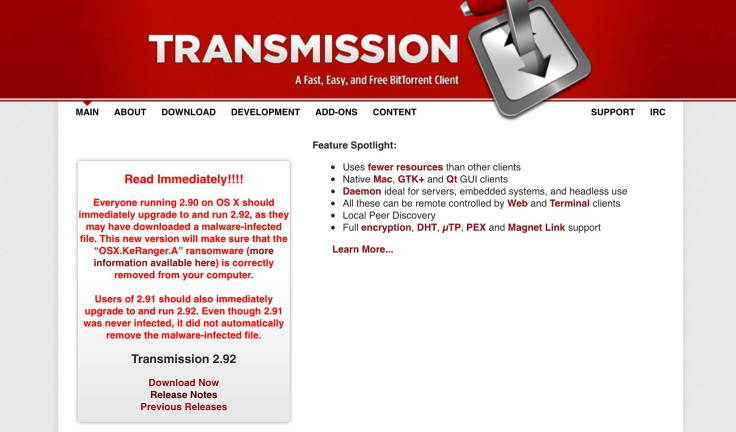
According to the company, the KeRanger infections occurred after users installed a poisoned version of Transmission 2.9 BitTorrent software. Users who installed the software on their Macs soon saw their files being encrypted while the nefarious hackers behind the malware then demanded a bitcoin payment worth about $400.
Mac users have long had a sense of security in believing that their computers “couldn’t get viruses ,” but in the recent past, that scenario has begun to change. Last fall, two serious bugs were unveiled that allowed malware to embed itself deep into the Mac OS and run with administrator privileges.
With the growth of ransomware over the last three years, it’s not surprising we are seeing the ransom-demanding viruses emerge even on the security touting Mac OS X platform.
How Did Hackers Manage To Infect Mac Computers With Ransomware?
Apple products are built on a fairly closed platform with a heavy vetting process for the apps and software found in its store. But the same level of protection doesn’t apply to projects that are open source and found outside of the Mac or iTunes store. This was the case with the ransomware infected Transmission software. Transmission is an open source project housed on the web.
But doesn’t Apple have some level of malware detection for programs downloaded from the web? Indeed, it does. According to researchers, the KeRanger ransomware was sophisticated enough in its design to evade detection.
“The KeRanger application was signed with a valid Mac app development certificate; therefore, it was able to bypass Apple’s Gatekeeper protection,” the company wrote in a blog on its findings .
The author of the KeRanger malware was also careful not to make it immediately obvious how the infection took place. After users install the infected Transmission app, it embed an executable file on the machine, but it waits for three days before connecting or “checking in” with the command and control servers run by the attacker. These servers are accessed via the Tor network so they can’t be traced to the author.
After making the connection, the malware then begins the job of encrypting document and data files on the victim’s system and then demands the one bitcoin (about $400) payment in order to decrypt the files.
KeRanger is a new kind of ransomware and appears to still be under active development say Palo Alto researchers. Besides just encrypting files on the computer, the ransomware appears to attempt encrypting Time Machine backups as well.
Palo Alto was quick to report the ransomware issue to Apple and the company swiftly revoked the certificate for the infected Transmission software while also updating the XProtect antivirus signature. Meanwhile, the Transmission Project has removed the malicious installers from its website and a new version of the Transmission software is now available.
In addition, Apple has made it so that going forward, anyone who installs an infected version of the software will receive a warning message on their screen saying either, “Transmission.app will damage your computer. You should move it to the Trash,” or, “Transmission can’t be opened. You should eject the disk image.”
How Can I Check If KeRanger Infected My Copy Of Transmission BitTorrent Software?
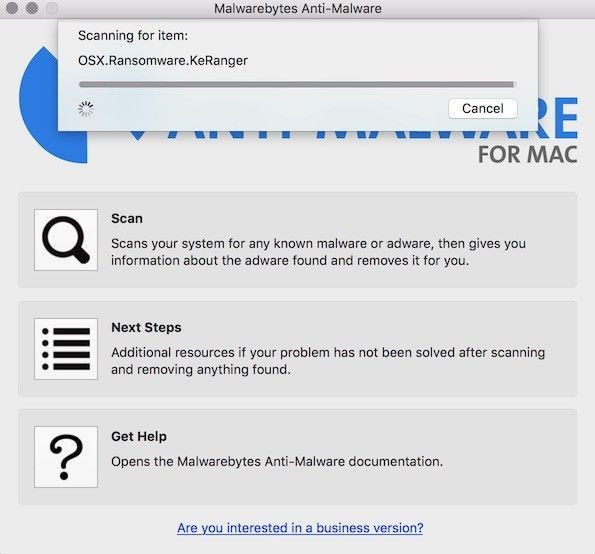
The ransomware infected Transmission files were downloaded after 2 p.m. EST on Friday, and before 10 p.m. EST Saturday. If you downloaded the 2.9 version of Transmission software between those time periods or you are concerned you might have been infected, Palo Alto has graciously provided some information for protecting yourself against the ransomware attack, which we've listed below. In addition, you can also use the Malwarebytes for Mac tool to detect and remove the ransomware.
Checking For KeRanger Ransomware On Mac
Go to Terminal or Spotlight.
Type in and check for one of the following two applications:
/Applications/Transmission.app/Contents/Resources/ General.rtf
/Volumes/Transmission/Transmission.app/Contents/Resources/ General.rtf exist.
If either file exists, you are using an infected version of Transmission.
How To Remove KeRanger Ransomware From Mac
Launch Activity Monitor (you can find it by searching spotlight)
Check if a process called kernel_service is running.
If kernel_service is running, double-click on it.
Select the Open Files and Ports pane to the right
In Open Files and Ports check for a file name that should look like:
/Users/
/Library/kernel_service’.
If this exists then you’ve found KeRanger’s main process.
Terminate the process using Quit>Force Quit
Search Spotlight for the ~/Library directory.
Open the Library directory and search for the files below. If they are present, delete them:
.kernel_pid,
.kernel_time,
.kernel_complete
kernel_service
You should also delete the version of the app on your computer by following these instructions or using AppCleaner .

![Best Gaming Mouse For Gamers With Smaller Hands [2025]](https://d.player.one/en/full/227430/best-gaming-mouse-gamers-smaller-hands-2025.png?w=380&h=275&f=fdcf47c1c5fc58d1e41d3be505c12568)















