Ransomware infections have seen exponential growth in 2016, as security researchers report both old encrypting malware like Cryptolocker and new versions like Locky are utilizing craftier methods to attack machines and encrypt files before victims even realize what’s happened. Victims are then forced to either pay the ransom or hope they have a backup recent enough to spare them any lost data. Meanwhile, the time required to remove ransomware and restore lost files can prove costly as well.
Over the months of January through March, several different forms of ransomware including Cryptolocker, Locky, TeslaCrypt, Petya and SamSam reared their ugly heads, taking captive millions of victims from small businesses to hospitals to major news sites like the New York Times , BBC and Newsweek .
But why the sudden upturn in successful ransomware attacks? Security researchers at a variety of firms report attackers are not only upgrading their malware to make it more unbreakable, they are also using unique methods of distributions. In some cases, these methods require no user interaction at all.
In the past, most ransomware infections occurred via phishing attacks, which require a user to click on a poisoned browser or email link. But these newer attacks are less dependent on user interaction and more dependent on unpatched problems or lax security practices.
iDigitalTimes spoke with researchers from Cisco Talos and Malwarebytes to discuss the rise in ransomware attacks and how they are changing.
Ransomware Evolution 2016: How File-Encrypting Malware Is Getting More Sophisticated
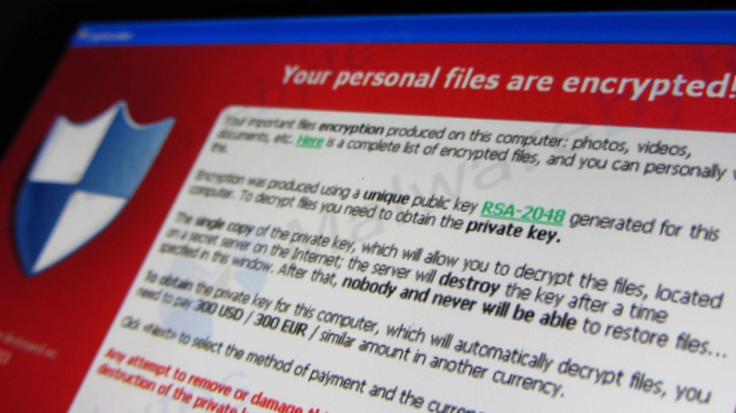
When ransomware first appeared, it largely targeted individuals and small businesses, but over time, attackers have upped the ante. They are now targeting major government and healthcare organizations as well as sites that see a massive number of visitors, such as online news publishers. As attacks hit larger targets, they are also becoming more sophisticated, using newer methods that are harder to detect or require less user interaction.
According to Cisco Talos, the company saw a spike in ransomware infections at multiple healthcare organizations in late March, but the attacks didn’t happen because a negligent employee clicked on a poisoned email link. Instead, the malware was distributed without employees doing anything at all. So how was it happening? Craig Williams, senior technical leader at Cisco Talos, says it happened because of unpatched servers inside the targeted organizations. Cybercriminals scanned the web looking for servers that neglected to patch a specific vulnerability and then attacked them.
“Up till now most ransomware we’ve seen required a person to interact with it to infect the system,” Williams said. “This is the first time we’ve seen traditional software being used to distribute ransomware.”
According to Williams, dozens of healthcare organizations contacted Cisco Talos about ransomware infections, which could have easily been avoided if the systems had been regularly updated.
“The frustrating thing about this is, in order to mitigate it all you have to do is follow standard best practices. Patch your servers. Have a backup. It’s that simple,” he said “A lot of people in the health industry don’t have proper administrators or a security staff so as a result things like backups aren’t happening. We think attackers are targeting health care because it’s an industry that will pay and has poor information security structure.”
Recent new stories support Williams’ theory about the healthcare industry. In February, a story broke about a California hospital paying $17,000 in bitcoin to cybercriminals to have patient files decrypted.
NEW: MedStar Health Joins Dozens More Healthcare Organizations Hit by Ransomware; Why File-Encrypting Malware Is Infiltrating Health Systems
The same weekend Cisco Talos saw these attacks, another type of ransomware attack was striking web users. Using the tried and true Angler malware kit, cybercriminals hijacked a number of ad networks, including Google’s, served malicious ransomware-installing ads to visitors at the New York Times , BBC, Newsweek and other major online publishers.
According to Malwarebytes researcher Jerome Segura, this particular attack was unique in that it used video ads to distribute its cocktail of malware among which were classic ransomware software like Cryptolocker, TeslaCrypt and Locky. Users didn’t need to click on the ad at all. Once the page loaded, the video began doing a drive-by malware installation on victims’ computers.
“We see a rise in malvertising attacks every weekend,” said Segura, “but this was really out of the ordinary in terms of the numbers of publishers that were affected and the ad networks that were involved. We’d never seen so many attacks happening all at the same time.”
Though the attacks only lasted about 24 hours, the impact was massive, said Segura. By using a sophisticated and unusual method of infection that went undetected even by Google ad networks, the campaign had widespread reach.
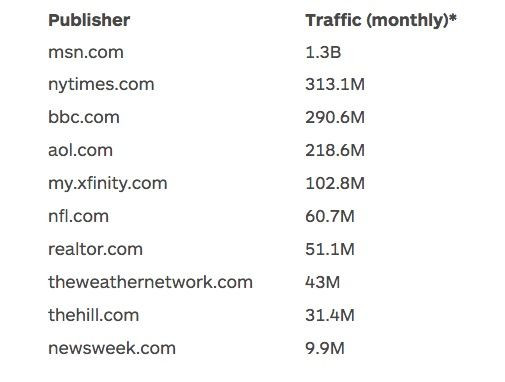
“The ads that were infected were video ads, which is why they made it through,” said Segura. “Most past malware attacks have happened via display ads or traditional ad banners, but this was a new vector and caught everyone by surprise.”
According to Proofpoint, the cyber security company that discovered malware was being served via video ads, affected users didn’t have to interact with the ad at all to be infected. The malware was distributed to users by simply visiting the site if they didn’t have their Flash Player, Silverlight and Internet Explorer software up-to-date.
Though the campaign has ended, Segura believes this isn’t the last we’ll see of video-transmitted ransomware.
“We are going to see a lot more of that now since this had such an impressive effect,” he said.


















