An ancient vulnerability in DNS servers leaves thousands of educational institutions vulnerable to hacking, say security researchers. In a briefing at HITB Haxpo in Amsterdam Wednesday, researchers Paul Mason, Kyle Fleming and Andy Gill, Penetration Tester at Dell SecureWorks, exposed a prolific weakness in the networks of educational institutes around the world. The problem is due to a 16-year-old vulnerability in DNS servers, which allows for zone transfers outside of the institution network.
Gaining access to network information via zone transfer is the first passive action an attacker takes in an effort to exploit and hack the private and sensitive data of any device on the network. In conducting a scan of some 10,000 educational domains, Mason, Fleming and Gill found 1,340 of them allowed for zone transfers leaving them wide open for attack.
What Is A Zone Transfer?
So why are so many domains coming up vulnerable to a bug that’s over 15 years old? The problem lies in the need to share information.
Zone transfers allow authoritative name servers inside networks to request and receive full copies of resource records for a particular zone on a given network. This is important, particularly when a institution wants the ability to share a lot of information amongst its users.
In a network, a zone acts as a database for a single DNS domain name – for example, google.com. If other subdomains (ie: mail.google.com) are added, they can become part of that domain and stored inside that same record, or they could belong to another zone.
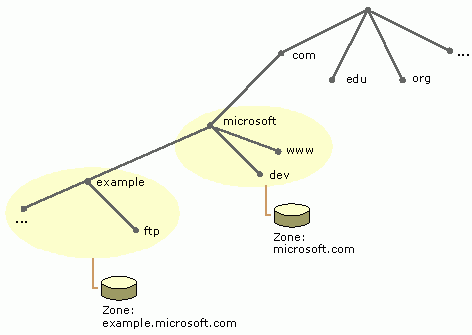
If there is a DNS server on the network that needs to be mirrored to another, a zone transfer can be performed.
Zone transfers inside the network can be useful for legitimate reasons like checking if IP addresses match up to names, or for sharing data. Inside of a college or university system, zone transfers may be desirable for sharing libraries and other essential resources to staff and students. On the dark side, however, allowing zone transfers also leaves system vulnerable to attacks if any of the authoritative name servers have been misconfigured.
Misconfigured, or “rogue” servers don’t operate in the way they should, and an outside attacker can ask for a zone transfer and the rogue server will give it to them with no questions asked.
Most networks have mitigated this problem by not allowing zone transfers on the network, but in a lot of educational institutes this is oddly not the case.
“You would have expected that not to exist any more you’d hope it wouldn’t exist anymore,” said Mason. “The one place that it exists, however, is in institutes like universities that are so desperate to be linked up to other universities they are constantly exchanging information with one another. There only needs to be one rogue DNS name server and you know every single device on the external facing network and in some cases, the internal network as well.”
Once the attacker has performed the zone transfer he or she is able to see all the devices that have ever been connected to the system up to the point of the zone transfer. Along with a variety of different records types -- some with very descriptive names. While at this stage attackers don’t have access to sensitive data like emails or identifying information about students, it is a major step in the attack chain.

“ From the perspective of a hacker you can build up a scope of what you want to attack, based upon information returned from an AXFR request,” said Gill.
So how can sys-admins mitigate problems with zone transfers? The simplest solution of course is not to permit them, but in the case that the network wants to continue allowing zone transfers, the best solution is to implement IP restrictions on who can request and receive a zone transfer. Additionally Fleming has written a tool to check your domain for vulnerability that is available now on Github at https://github.com/radman404/DNSTeller
To learn more about the work of Mason, Fleming and Gill check out the full presentation slides here.
For More OSX, iOS, Jailbreak And Infosec News
Follow Cammy on Facebook, Twitter, or Google Plus
Send tips to c.harbison@idigitaltimes.com
GPG Key ID: 56E784D9














![[EG April 19] Best 'Stardew Valley' Mods That Will Change](https://d.player.one/en/full/226012/eg-april-19-best-stardew-valley-mods-that-will-change.png?w=380&h=275&f=955520b8313253ee3c39c791f6210f38)



