The latest malware making the rounds on Android smartphones is called “Gooligan,” and it has potentially infected more than one million devices worldwide, according to security agency Check Point. The number of compromised devices is reportedly increasing by 13,000 per day.
The agency has been tracking the malware for at least one year, after discovering Googlian’s malicious code within the SnapPea app. The code was also associated with other malware, including Ghostpush, MonkeyTest and Xinyinhe, but has strengthened after a period of dormancy in 2015 to its current iteration.
Check Point detailed the history and prospects of Gooligan in a research report published Wednesday.
What does Gooligan do?
Gooligan is a malware that aims to access data from Google services such as Google Play, Gmail, Google Photos, Google Docs, G Suite, Google Drive and others by gaining root access to devices and stealing authentication tokens from other applications.
Once a user downloads an app infected with Gooligan, the malware will download a rootkit, such as VROOT or Towelroot, which are still able to access exploits on older Android versions not supported on current security updates. Once Gooligan has root access on a device, it can download a malicious module onto the device, which then injects Gooligan code into various Goole run applications.
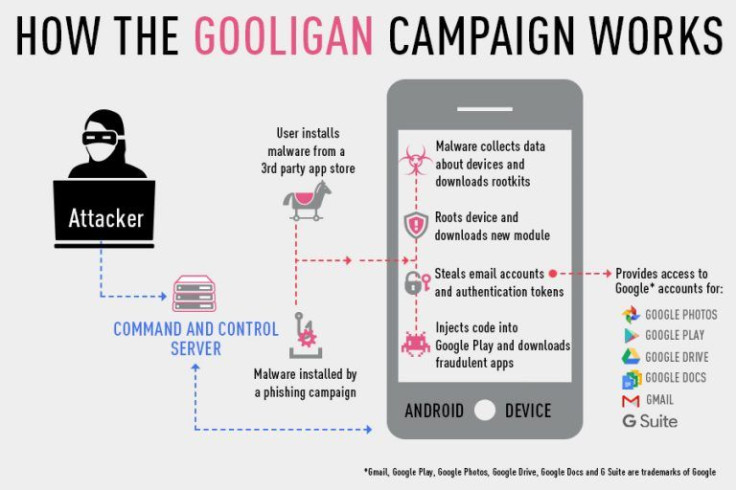
With this infection method, Gooligan can gain control of a user’s Gmail account and Android authentication token details. Authentication tokens confirm a successful login to various apps and services. If compromised, malicious users can fake a login to gain access to an original users’ accounts and information.
Gooligan also can install infected apps to submit fake reviews and higher ratings to promote further downloads. The malware lists these fake apps within a device’s Appendix A. Such applications include Perfect Cleaner, WiFi Enhancer, Memory Booster, Multifunction Flashlight and Simple Calculator. Find a complete list of fake Gooligan apps here.
Gooligan can also install adware to to generate revenue through ads.
What Android smartphones are most at risk?
Android smartphones running software in the Jelly Bean, KitKat and Lollipop versions are most at risk. This puts up to 74 percent of Android devices at risk for infection by Gooligan. Devices most at risk are those in Asia at 57 percent, due to users in this region having a propensity for third-party app stores. Gooligan is then most prevalent in the Americas at 19 percent, Africa at 15 percent and Europe at 9 percent.

How will I know if my Android smartphone is infected with Gooligan?
Users can check their applications list for any of the fake Gooligan apps. Users can also use Check Point’s Gooligan detection tool to determine if their Gmail address has been compromised.
What do I do if I my Android smartphone is infected with Golligan?
Users must flash a clean version of Android software onto their smartphones. Those who are not tech savvy should get assistance from a certified technician or their mobile carriers. Users should also change the passwords on their Google accounts.
What you can do to protect your Android smartphone
Avoid third-party app stores. Only download apps from official sources like the Google Play Store.
Only download apps from trusted developers.
Update your device to the latest Android software (Android 6.0 Marshmallow or Android 7.0 Nougat) if possible.
Gooligan Prognosis
Google is currently working with Check Point to ensure Gooligan does not become a serious threat to Android users on a broad scale. While some users have discovered Gooligan on their smartphones, Google has found no evidence of data breaching and attack targets, Adrian Ludwig, Google’s director of Android security stated in a Google Plus post.
To help secure Android as a whole Google has developed the Verify Apps mechanism, which alerts users of the download of malicious applications, even from third-party app stores. The Android team has also worked to remove fake Gooligan apps from the Google Play Store.
Google is also working with users whose devices have been infected by Gooligan to ensure they can securely sign into their devices. Finally, the tech giant has continued efforts with internet service providers to identify and take down the virtual infrastructure that hosts such malware.
















